UTM – Unified Threat Management

UTM – Unified Threat Management
Unified threat management (UTM) is an approach to information security where a single hardware or software installation provides multiple security functions. This contrasts with the traditional method of having point solutions for each security function. UTM simplifies information-security management by providing a single management and reporting point for the security administrator rather than managing multiple products from different vendors.UTM appliances have been gaining popularity since 2009, partly because the all-in-one approach simplifies installation, configuration and maintenance.[4] Such a setup saves time, money and people when compared to the management of multiple security systems. Instead of having several single-function appliances, all needing individual familiarity, attention and support, network administrators can centrally administer their security defenses from one computer. Some of the prominent UTM brands are Cisco, Juniper, Fortinet, Sophos, DwarPal, SonicWall and Check Point.
UTM – Features
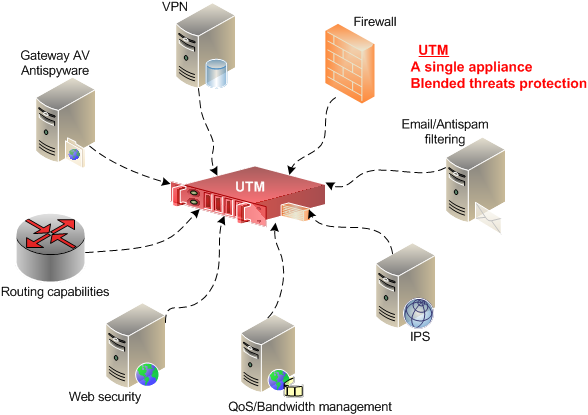
UTM – Features
UTMs at the minimum should have some converged security features like
Network firewall
Intrusion detection
Intrusion prevention
Some of the other features commonly found in UTMs are
Gateway anti-virus
Application layer (Layer 7) firewall and control
Deep packet inspection
Web proxy and content filtering
Email filtering
Data loss prevention (DLP)
Security information and event management (SIEM)
Virtual private network (VPN)
Network tarpit
Disadvantages
Although an UTM offers ease of management from a single device, it also introduces a single point of failure within the IT infrastructure. Additionally, the approach of a UTM may go against one of the basic information assurance / security approaches of defense in depth, as a UTM would replace multiple security products, and compromise at the UTM layer will break the entire defense-in-depth approach.
What is unified threat management (UTM) software?
Unified threat management devices provide small and midsize businesses with multiple network security functions in a single appliance. SMB buyers should carefully evaluate UTMs’ performance when numerous security functions are enabled, and UTMs’ ability to handle new SMB practices. Gartner defines the unified threat management (UTM) market as multifunction network security products used by small or midsize businesses (SMBs). UTM products must continually add new functions, and therefore encompass the feature set of many other network security solutions, including next-generation firewall, intrusion prevention systems (IPSs), secure Web gateway and secure email gateway. While consolidation comes with compromises in performance and capability, these are compromises that many SMBs are willing to accept.
 Firewall Support Company in India All type of Firewalls Support Provider Company in India
Firewall Support Company in India All type of Firewalls Support Provider Company in India


































