In early August, malware infiltrated the computer network and systems of a transmission plant in North Carolina. It was a potentially costly attack, as the factory stood to lose $270,000 for every hour that it wasn’t manufacturing and shipping its automotive parts to plants across the U.S. Fortunately, the facility had a firewall standing between the factory’s crown jewels and hackers, blocking the malware when it tried to exit their network.
Just like the structure they were named after, firewalls are the first line of defense against cybercriminals. They check, control, and block incoming or outgoing network traffic. Data traversing in and out of your systems must first pass through the firewall, scrutinizing them or blocking them if they don’t meet specified criteria.
But maintaining your company’s firewall can be daunting especially if the network it protects has arrays of clients, endpoints, servers, and other devices, each of which has their own connection requirements. If improperly managed or deployed, a firewall can leave gaps in your organization’s security that attackers can use to infiltrate your network. Gartner even projected that in the next three years, 99% of firewall breaches would be caused by misconfigurations.
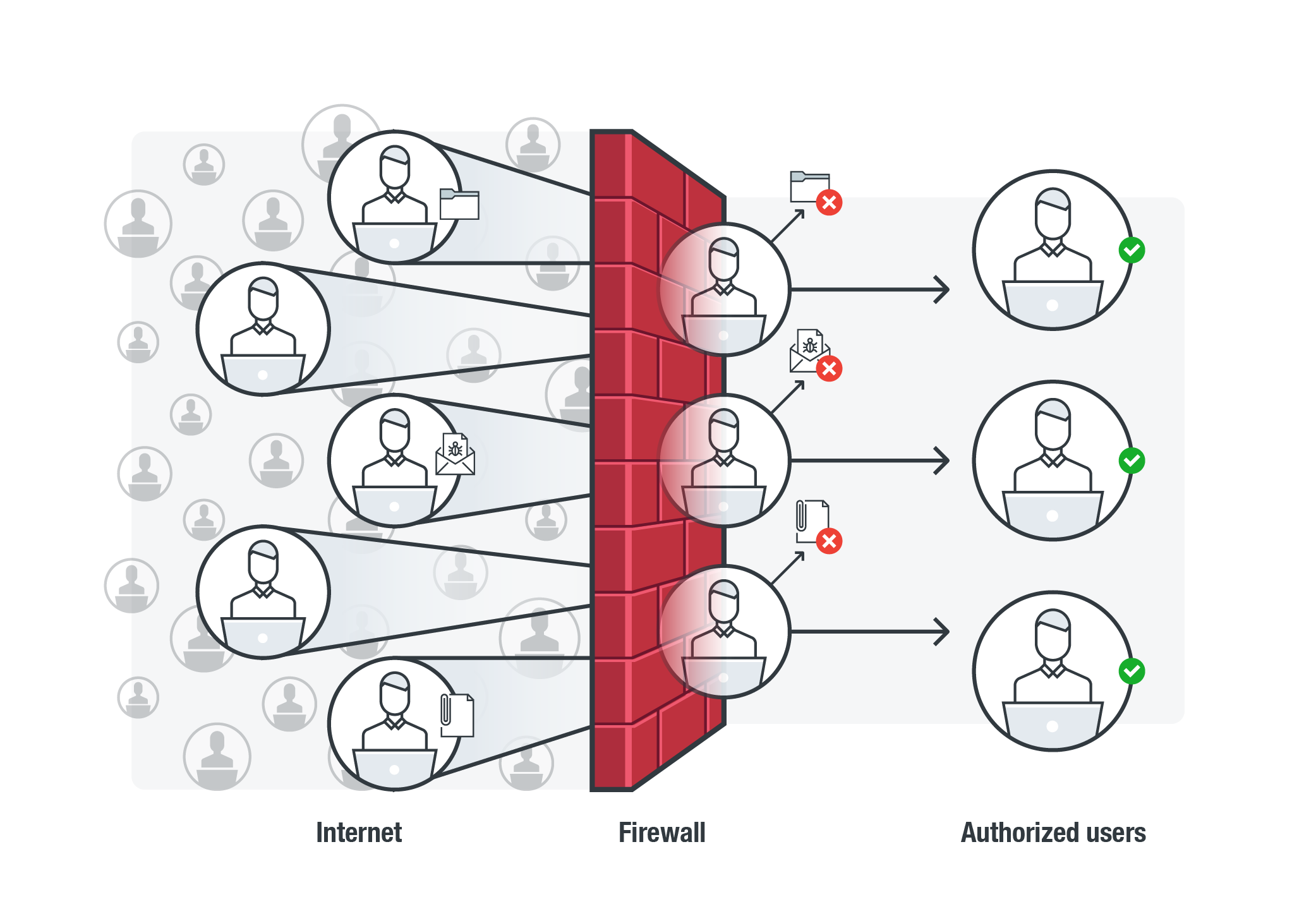
Firewalls serve as your first line of defense: they scrutinize inward or outbound traffic for any malicious content as per your rules.
There is no panacea for building a hacker-proof firewall, but there are things that can be done to streamline its management. Every organization has unique and specific requirements but these can provide you with a starting point for managing your firewall—so you and your company don’t get burned.
What firewall fits you?
Firewalls can be network or host-based. Network firewalls are arrayed on the gateways—computers routing traffic from a workstation to an external network—such as those within local and wide area networks (LANs/WANs) or intranet. Host-based firewalls, which became significant when it was integrated into Windows XP back in 2004, are positioned in communication endpoints and part of your operating system (OS) or security application.
They vary depending on where communication originates and where it is inspected and intercepted. Weigh your options and define your security needs. What do your networks and systems require? What kind of transactions transpire within your networks? Will they have the resources to run it? Who will manage your firewall? Will it be enough to contain and prevent incursions?
Enforce the principle of least privilege
The same concept applies when deploying firewalls. Applying the principle of least privilege reduces the firewall’s attack surface. Deny all incoming and outgoing traffic by default first, then build up your rules by enabling only the services whose traffic you want in and out. Disable services or software that aren’t needed and limit the applications that run on the firewall.
Strengthen your firewall rules
Periodically spring-clean your firewall’s policies to maximize its performance and eliminate conflicting rules. But more importantly, it lets you audit your firewall’s architecture and streamline it if needed.
The SANS Institute has a checklist of rulesets that can serve as your benchmark. Ensure that your firewall enables anti-spoofing filters and user and management permission rules, i.e., allowing HTTP to a public web server or Simple Network Management Protocol (SNMP) traps to network management servers. Make your firewall more efficient by running noise rules—dropping unwanted traffic. Rules that notify IT/system administrators of suspicious traffic are recommended. Log the traffic for analysis; back these logs up and store them in secure repositories.
Is your firewall application-aware?
An effective firewall doesn’t just involve creating the right policies, but also proactively analyzing the connections and filtering packets of data that pass through it. Ensure that your rules can identify the conditions within the connection, predict what it will entail, and detect disruptions in a normal connection. You can use these as your starting points when filtering traffic: direction, (inbound/outbound), protocol (TCP/UDP/ICMP/ICMPv6), as well as destination computer and ports.
Many of today’s software and applications don’t employ standard ports—nodes of communication for a specific process or service. Many malware also use them as entry points: WannaCry, and the other malware after it—UIWIX ransomware and certain cryptocurrency-mining malware—used Port 445. Enforce port restrictions, but balance the business need to access certain services. The SANS Institute also has a checklist of ports that can be blocked. It’s also recommended that your firewall can inspect and classify the traffic by applications on the ports that you permit, open or use.
Keep everyone in the loop
Make sure that administrators, risk/compliance managers, and information security professionals who maintain the firewall know the policies configured. Opening a port can contradict corporate or security policy, for instance, and in-house application developers or those provisioning certain services may also request changes to firewall policies. Make sure that everyone is in the loop and following good documentation practices. Define the purpose of opening a new port or what the new rule is for, and who will be affected by the changes. These considerations help mitigate misconfigurations and conflicting rules in your firewall.
Firewalls should be part of defense in depth
As hackers and threat actors fine-tune their attacks, so must the technologies that protect the data and systems they’re after. Firewalls are also now being incorporated with other functionalities such as deep packet inspection—which examines the packet of data for malware and other defined policies—as well as intrusion prevention and detection systems.
Firewalls can be an effective preventive measure against threats, but they shouldn’t the only layer of protection. Firewalls can’t protect you from email-based threats and unauthorised access to devices, for instance. While they help secure your networks and systems by validating and blocking suspicious traffic, they are just a starting point for building your organization’s cybersecurity defenses.
 Firewall Support Company in India All type of Firewalls Support Provider Company in India
Firewall Support Company in India All type of Firewalls Support Provider Company in India











