First step to better data security: Know who’s getting access to your cloud data

What’s common between Uber, Cisco, and some of the recent high-profile data breaches, is MFA fatigue – an exploit through which attackers utilized multi-factor authentication solutions and bypassed vulnerabilities to gain access to the company’s cloud services and network.
These incidents reveal an alarming trend: even after being proactive in managing privacy and data protection compliance in the cloud, enterprises are still grappling to get 100% control of their entire attack surface, 80% of the attacks are happening due to credentials abuse.
Cloud creates untenable and continuous data exfiltration risk. People and the lack of visibility have emerged as the weakest links as they affect companies of all sizes.
It’s helpful to understand what happened during a few recent breaches in order to be ready with the right defences. So let’s walk through typical data breach incident and gather our learnings:
Toxic combinations that enable the attacker to exploit data
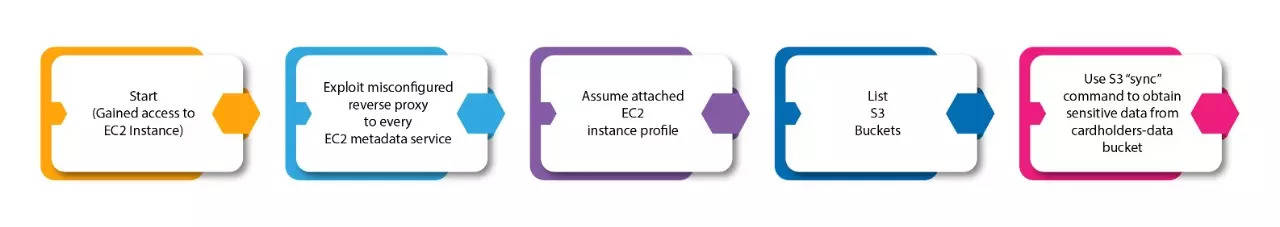
In most organizations that are transitioning to the cloud from the premise, it has been observed that the threat actor finds access to an Amazon Elastic Compute Cloud, or EC2 instance, through malicious ways and after conducting preliminary surveillance realizes that EC2 is acting as a reverse-proxy server.
Post some research, the threat actor makes use of client URL, or cURL, to send a request to the web server and establish the host header to the IP address of EC2 metadata services. The threat actor’s specially-curated URL request turns successful, enabling the access key ID, secret access key, along with the session token of identity and access management (IAM) instance profile to be shared with the EC2 instance.
The threat actor is armed with IAM’s role credentials and is now able to explore the target’s cloud environment with powerful permissions granted to the role. Finally, he has got access to the treasure, he can now list, identify and access the target’s private S3 Bucket. The threat actor not only has access to a plethora of sensitive information but can now download these to their respective local machines for malicious use.
Why are leading global enterprises becoming easy victims of these breaches?
As we all know, DevOps is all about creating robust software with better speed – specially in a cloud-native environment which is more about bringing innovation to market faster and transforming organizations. DevOps is the process of aligning the two Ps (people and processes) with technologies to give an unmatched boost to their speed and efficiency.
As per reports, DevOps teams experienced 200x more deployments, 2555x faster lead times, 24x faster recoveries from failure, 3x lower change failure rates and 22% less time spent redoing work.
The innovation triggered by DevOps has accelerated the pace of speed of software development, a new application can be built at a lightning speed. However, all the new applications are creating complexity in the cloud environment. Given the scale of corporate data stored in the cloud, cloud apps have become a top shadow IT risk for businesses.
According to an Oracle report titled Putting Cultural Transformation at the Heart of Cloud Success, more than 60% of a company’s overall IT spend is being driven by individual business units versus traditional IT departments.
Data silos are created as a consequence of decentralized IT spending. When data is held in apps outside the control of IT, the task of securing that data becomes more challenging.

Left unattended, these data silos can lead to costly data breaches. If IT can’t see or control sensitive corporate data stored on unauthorized cloud-based applications, that data is not secure.
An application can be concurrently used on multiple environments such as Google Cloud platform or Microsoft Azure, which will create number of identities – human and non-human, including access keys, employee credentials, passwords, bots. The big challenge before the organizations is manage these identities.
Cloud compliance and governance
While leading cloud providers adhere to well-known accreditation programs as PCI 3.2, NIST 800-53, HIPAA and GDPR, given the poor visibility and dynamics in the environment, most of the organizations are unable to keep up with the compliance audit process.
How IT teams can control access and protect systems without having visibility into their assets?
Shadow data and shadow identities are posing to be a nightmare for security teams considering they have no knowledge about what data is potentially leaving the business and the security of unauthorized platforms.
Organizations are grappling to get the visibility – to understand who has access to the data and under what circumstances; which identities are working in their cloud infrastructure environment.
There are few tools that now provide visibility in a siloed manner about the data, the identities and even their security postures, but these tools leave customers more confused as the customer has to make a decision to take action on their alerts.
This rise of cloud-native applications stemmed from a series of cybersecurity solutions. Some were born new to serve the age of the cloud including cloud monitoring, workload protection, infrastructure entitlement management, etcetera.
However, none of these solutions are capable of covering key problems – governance of cloud.
The security teams need an agile and new-age-security solution that would provide a holistic approach to keep up with the evolving threat landscape with more sophisticated techniques.
Continuous governance is the way forward, as we all agree that with the cloud the surging demand for access in conjunction with a lack of governance and visibility into identity and data risks is certainly creating a gap that can only be resolved through continuous governance.
In addition to the various cloud monitoring solutions security tools that provide general visibility and are extensively focused on infrastructure and configuration, we need an evolved approach focusing on providing visibility to the most important asset; data, and providing governance of identities that can access these data assets.
Establish a concept of ‘exploitable access’
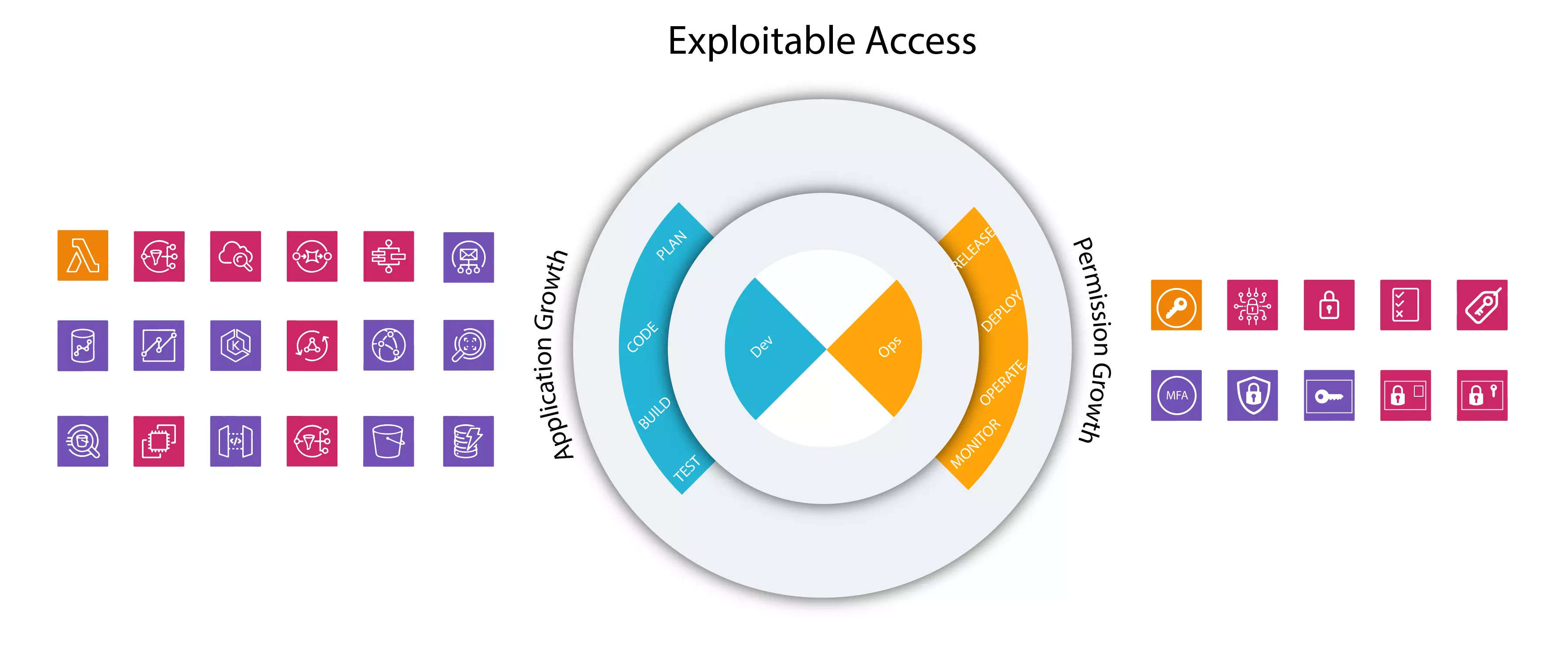
What’s required is to combine data, identities, network, applications, and policies together to build a context of how they are connected in the cloud by creating ‘exploitable access’. Build a prioritization of risks that can now be seen and remediate those by inserting ‘policy as code’ to ensure the same risks don’t show up again by:
- Consistent monitoring of who has & who is accessing your data assets.
- Detection of attack paths to critical resources & remediation.
- Quantifiable risk scoring of data assets and identities.
- Prioritizing remediation based on the risk of exposure and exfiltration of data.
- Measuring the maturity of policy enforcement & violations.
- Provide enterprises an exhaustive and honest assessment of their cloud identity risks.
- Ensure that organizations that have implemented highly automated DevOps identify appropriate security controls and have embedded them in the code and templates early in the development cycle.
- Granular privilege provides key management: Track and provide a dashboard of active and track active and inactive identities, their roles, their usage, whether are they over-provisioned or dormant (because of the employee exit) may be captured, and not go unnoticed and can significantly prevent a potential breach.
- Identify applications, networks, resources, user, policies & their relationship in the cloud account.
With the demand for access to resources and data in the cloud growing exponentially, enterprises must focus on sharpening identity governance as visibility of risks in cloud data access and identities is the way forward to security and governance in a cloud-native environment.
This is a contributory article authored by Ambrish Deshpande, COO & Co-founder of Stack Identity.
 Firewall Support Company in India All type of Firewalls Support Provider Company in India
Firewall Support Company in India All type of Firewalls Support Provider Company in India











