Three waves of DNS hijacking attacks against consumer routers have been linked back to Google Cloud Platform abuse.
Hackers have been abusing Google’s cloud computing service to redirect and intercept web and mail traffic on an array of vulnerable consumer routers.
A researcher said that he has seen the Google Cloud Platform being abused to carry out three separate waves of DNS hijacking attacks over the past three months targeting D-Link, ARGtek, DSLink, Secutech, and TOTOLINK routers. DNS hijacking is an attack that causes router traffic to be redirected and sent to malicious websites.
“All exploit attempts have originated from hosts on the network of Google Cloud Platform,” said Troy Mursch with Bad Packets Report in a Thursday report. “In this campaign, we’ve identified four distinct rogue DNS servers being used to redirect web traffic for malicious purposes.”
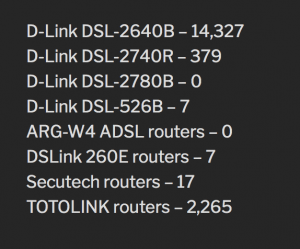
The first wave was launched Dec. 29 and targeted D-Link DSL-2640B, D-Link DSL-2740R, D-Link DSL-2780B and D-Link DSL-526B, redirecting their traffic to a rogue DNS server in Canada. The second wave of attacks, launched Feb. 6, also targeted these same types of D-Link modems and was also redirecting traffic to a DNS server in Canada.
The third and latest wave, on March 26, targeted ARG-W4 ADSL routers, DSLink 260E routers, Secutech routers, and TOTOLINK routers. This campaign redirected traffic to two rogue DNS servers, both hosted in Russia.
While Mursch couldn’t list how many routers were specifically impacted, he said that more than 14,000 D-Link DSL-2640B routers were exposed to the public internet, and 2,265 TOTOLINK routers. The researcher also did not specifying specifically how adversaries attacked the routers. However, he pointed out that in years past the DNSChanger malware has been prolific, raking in $14 million in advertising-related fraud for cybercriminals behind it.
The various waves of attacks have all used Google Cloud Platform hosts.
Attackers first used Google’s cloud service capabilities to scan for vulnerable routers that could be exploited. Other researchers have noted domain parking remains a booming business often tied to illicit activities.
They then used Google’s platform to remotely configure the routers to their own DNS servers, using malicious code.
It is easy to abuse this platform, said Mursch – anyone with a Google account could access a “Google Cloud Shell” machine easily, a service that provides users with the equivalent to a Linux VPS [Virtual Private Server], giving them root privileges directly in a web browser.
Also making the attacks easy is the fact that Google is slow to respond to reports of abuse, he said.
“Being a large cloud service provider, dealing with abuse is an ongoing process for Google,” Mursch said. “However unlike their competitors, Google makes it very easy for a miscreants to abuse their platform.”
Google did not respond to a request for comment from Threatpost.
DNS hijacking attacks redirect queries to a domain name server via overriding a computer’s transmission control protocol/internet protocol (TCP/IP) settings – generally by modifying a server’s settings. These types of attacks could help bad actors carry out advertising-related fraud or phishing attacks, Mursch said.
The attacks could have more insidious purposes as well. In January, a slew of attacks aimed at multiple government domains triggered the Department of Homeland Security to issue an emergency directive ordering all federal agencies to urgently audit Domain Name System (DNS) security for their domains.
Mursch for his part stressed that consumers keep their home router firmware up-to-date to prevent exploits.
“When security vulnerabilities are discovered, they are usually patched by the manufacturer to mitigate further attacks,” he said. “It’s also advisable to review your router’s DNS settings to ensure they haven’t been tampered with.”
 Firewall Support Company in India All type of Firewalls Support Provider Company in India
Firewall Support Company in India All type of Firewalls Support Provider Company in India